16 December 2019
Keeping corporate reputations safe and finances sound against cyberthreats
Introduction
Over ten years ago, the Chartered Institute of Management Accountants issued a corporate reputation report. Most strikingly, the section on reputational damage made no reference whatsoever to cybersecurity. However, fast forward to the present day and in the intervening period we’ve seen corporate reputations shattered by security breaches.
We’re in an age where zero-day attacks test companies’ best-prepared cybersecurity defences, while data thefts threaten the sanctity of their customers’ personal data. Regulatory regimes like GDPR are making failing in such matters incredibly expensive, a KYND report on cybersecurity in the legal sector shows a surprising number of companies but lack the preparedness for sophisticated, malicious cyberattacks.
Cybersecurity or lack of it can result in a catastrophic losses, but offering an exciting customer experience (CX) takes transparency and openness. Failing to achieve a balance between those opposing forces could see a company end up with irritated, unforgiving customers.
The corporate reputation construct
Fombrun (1996) defines corporate reputation as a snapshot that reconciles multiple images of a company for all its stakeholders. The Fombrun corporate reputation chart can be used as a tool to achieve the route to best practice. Although devised over 20 years ago, it still stands the test of time.
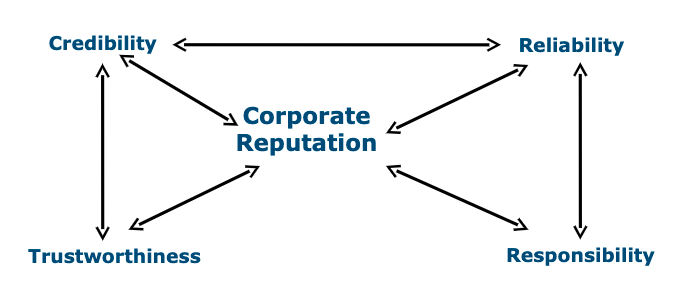
Figure 1: The Fombrun corporate reputation chart
Since then, various scholars have added to this, Chun (2005) draws on a set of attributes that reflects results of past behaviour of the organisation, its ability to satisfy expectations and, based on those expectations, to develop value for stakeholder groups.
So, although the brand and its equity mustn’t be damaged, perhaps through reputational misadventure, investment in branding isn’t synonymous with investment in reputation. An example of this is Ryanair as ‘the brand we love to hate’, showing the possibility of simultaneously having a strong brand but a poor reputation.
The potential punitive financial effects of GDPR
In 2017, Telehouse UK published an infographic of the 12 worst cybersecurity breach scenarios. The report said 90% of CEOs believed such transgressions had a negative impact on stakeholder trust, resulting in “some of the most impactful downturns in sentiment for an organisation”. Produced before the recent high-profile cybersecurity cases mentioned below, companies and customers alike are now being forced to really think about cybersecurity.
In 2018, Elizabeth Denham, Information Commissioner, said: “When an organisation fails to protect it from loss, damage or theft, it is more than just an inconvenience. That is why the law is clear – when you are entrusted with personal data, you must look after it. Those that don’t will face scrutiny from my office to check they have taken the appropriate steps to protect fundamental privacy rights.”
Those are strong words. However, the following recent examples taken from various reports in the public news media show how big the problem might be.
- Cambridge Analytica triggered tech industry year of reckoning: In March 2018, millions of Facebook profiles were hacked into. Cambridge Analytica used that data to predict and influence choices at the ballot box. A whistle-blower explained: “We built models to exploit what we knew about them and target their inner demons.” Facebook experienced a prolonged negative effect on its corporate reputation.
- TSB took its eye off the software update ball: TSB suffered a data breach in April 2018, A reported £30,000 was lost after fraudsters successfully posed as TSB staff investigating fraud. Some individuals even received text messages with verification codes. TSB promised no customer would be left out of pocket.
- Google escapes potential PR headache: In August 2018, Google announced it would be shutting down Google+. The Wall Street Journal reported a bug in the API for Google+ had been allowing third party-app developers to access data not just of users but also of their friends. Google fixed the bug but hastened the Google+ termination date.
- BA sent shivers down companies’ spines: £183 million, the highest fine the Information Commission Office has issued, was levied on BA in July 2019, as the first attack made public since the new GDPR rules were instated. Users of the British Airways website were diverted to a fraudulent one, with details of 500,000 customers harvested and approximately 380,000 transactions affected.
These examples are only the tip of the iceberg. Other notable occurrences include Capital One, Walmart Canada, Merck and the NHS. And, right at the end of 2019, came the UK government’s accidental online publication of personal details of people on the honours list.
The General Data Protection Regulation (GDPR) regime came into force in 2018 and was the biggest data privacy shake-up in 20 years. Until then the biggest penalty was £500,000 (the maximum under the old data protection rules) imposed on Facebook for its role in the Cambridge Analytica data scandal.
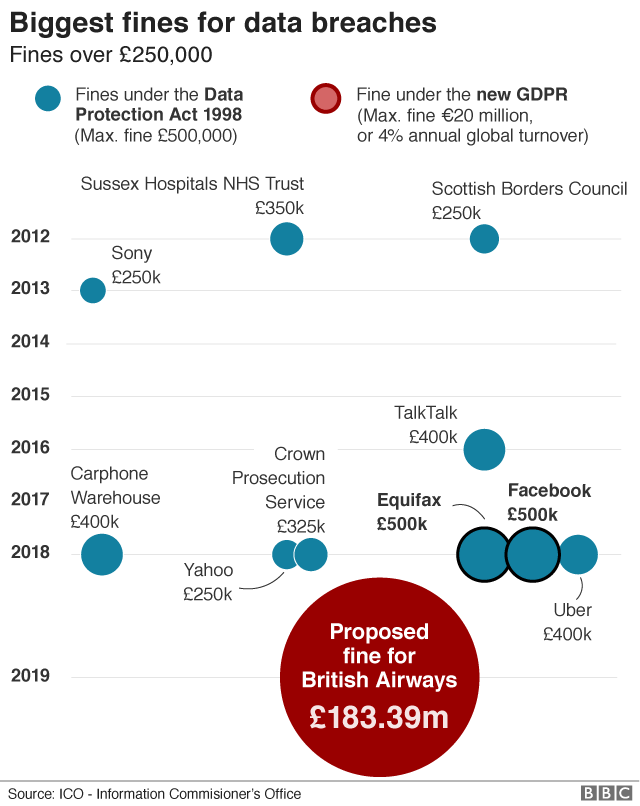
Figure 2: Biggest fines for data breaches (BBC, 2019)
The emergence of risk-based cybersecurity
Just like the Terminator, cybersecurity threats keep coming back stronger e.g. the emergence of spear-phishing and typo-squatting. With the launch of 5G, the Telehouse figure of one-third of data living in or passing through the cloud by 2020 is certain to be surpassed. Potential use cases of this latest ‘G’ mean cybersecurity should be at the forefront of business strategy especially in this era where mistakes aren’t easily forgiven.
A McKinsey article from 2019 calls for a risk-based stance to cybersecurity, which means that to decrease overall enterprise risk leaders must identify and focus on the elements of cyber risk to target, rather than the traditional maturity-based approach. What’s the difference?
Being maturity-based means focusing on building capabilities around what’s already known (hence, maturity) whereas being risk-based means dealing with the present, while understanding and prioritising emergent risks (including but not limited to cyberthreats).
The McKinsey article goes on to say that, at the moment, attackers benefit from organisational indecision on cyber risk – including the prevailing lack of clarity about the danger and failure to execute effective cyber controls. Leaders must identify and focus on the right risk elements to target. “The reality is that some applications represent more serious vulnerabilities – and therefore greater potential for risk – than others,” said McKinsey.
Conclusion
Corporate risk refers to the potential for business losses of all kinds – financial, operational, productivity-related, regulatory-related and, of course, reputational. Debilitating attacks on high-profile institutions are proliferating globally, and enterprise-wide cyber efforts are needed now with great urgency. It is widely understood there is no time to waste: business leaders everywhere, at institutions of all sizes and in all industries, are earnestly searching for the optimal means to improve cyber resilience.
A B2B Marketing blog states that for revenue generation, the average influence of the brand is 23%, while 94% of customers are likely to show loyalty to a brand that offers complete transparency. So, the connection of damage to the corporate reputation negatively affecting the brand image is undeniable. Gartner reported in 2019 that those truisms have led to an environment in which by 2020, 100% of large companies will be asked to report to boards of directors on cybersecurity and technology risk at least annually, up from 40% in 2018.
If you were to take one thing away from this post, it should be the importance of creating and maintaining a strong corporate reputation. And in no way allowing lack of cybersecurity to jeopardise that. It’s clear an explanation of your security posture is an essential weapon in your reputational armoury.
